Welcome to our comprehensive guide on Cloud Workload Protection Platforms (CWPP)! If you’ve heard the term CWPP before and found it confusing, you’re not alone. Many people are unsure of what exactly CWPP entails and how it can benefit their organization. In this article, we will demystify CWPP and provide you with a clear understanding of what it is, why it’s important, and how it can help protect your cloud workloads. So sit back, relax, and let’s dive into the world of CWPP together.
Understanding Cloud Workload Protection Platforms
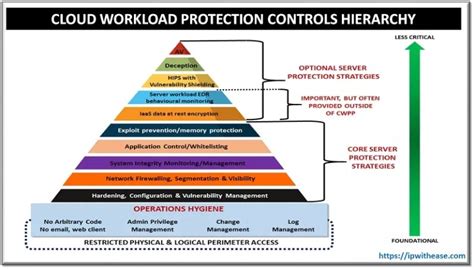
Cloud Workload Protection Platforms (CWPP) are security solutions designed to protect workloads running in the cloud. These platforms help organizations secure their data, applications, and infrastructure in cloud environments from various cyber threats. CWPP solutions provide visibility into the security posture of workloads, detect and respond to threats, and ensure compliance with security policies.
One of the key features of CWPP is workload protection, which involves securing individual workloads or virtual machines in the cloud. This includes protecting data stored in these workloads, ensuring secure communication between workloads, and preventing unauthorized access. CWPP solutions use a combination of technologies such as network security, endpoint security, data encryption, and identity and access management to safeguard workloads from cyber attacks.
CWPP platforms also offer continuous monitoring and threat detection capabilities to identify malicious activities and anomalies in real-time. By analyzing network traffic, user behavior, and system logs, these solutions can proactively detect and respond to security incidents before they escalate. With the rise of sophisticated cyber threats targeting cloud environments, CWPP plays a crucial role in enhancing the overall security posture of organizations.
In addition to workload protection, CWPP solutions provide visibility and control over security configurations and compliance policies. Organizations can use these platforms to monitor the security status of their cloud workloads, identify misconfigurations, and enforce security policies to ensure compliance with industry regulations and internal security standards. CWPP solutions also offer reporting and auditing capabilities to track security events and demonstrate compliance to auditors and regulators.
Another important aspect of CWPP is automation and orchestration, which helps organizations streamline security operations and response processes. By automating routine tasks such as threat detection, incident response, and security policy enforcement, CWPP solutions enable security teams to focus on more strategic initiatives and reduce the time and effort required to manage security in the cloud. This automation also helps organizations scale their security capabilities as they expand their cloud footprint.
Overall, Cloud Workload Protection Platforms are essential components of a comprehensive cloud security strategy. By providing workload protection, threat detection, compliance management, and automation capabilities, CWPP solutions help organizations secure their cloud environments and mitigate the risks associated with cyber threats. As organizations continue to adopt cloud technologies and migrate workloads to the cloud, investing in a robust CWPP solution is crucial to ensure the confidentiality, integrity, and availability of their data and applications.
Features and Capabilities of CWPP
Cloud Workload Protection Platform (CWPP) offers a variety of features and capabilities to help organizations secure their cloud workloads and data. One of the key features of CWPP is its ability to provide real-time visibility into the security posture of your cloud workloads. This means that you can easily see which workloads are at risk and take immediate action to protect them. CWPP also offers advanced threat detection capabilities, allowing you to identify and respond to potential security threats before they can cause any damage.
Another important feature of CWPP is its ability to provide granular control over your cloud workloads. This means that you can set specific security policies for each workload, ensuring that they are protected according to your organization’s unique security requirements. CWPP also offers automated remediation capabilities, allowing you to quickly and easily address any security issues that arise.
CWPP also offers comprehensive compliance monitoring capabilities, allowing you to ensure that your cloud workloads are compliant with relevant regulations and industry standards. This can help you avoid costly fines and reputational damage that can result from non-compliance. Additionally, CWPP offers integrated threat intelligence feeds, allowing you to stay up-to-date on the latest security threats and vulnerabilities.
Overall, CWPP offers a robust set of features and capabilities that can help organizations secure their cloud workloads and data. From real-time visibility and advanced threat detection to granular control and automated remediation, CWPP has everything you need to keep your cloud workloads secure and compliant.
Benefits of Implementing a CWPP
Implementing a Cloud Workload Protection Platform (CWPP) offers a wide range of benefits to organizations looking to enhance their security posture in the cloud. From proactive threat detection to compliance monitoring, a CWPP can provide the necessary tools and capabilities to protect workloads and data in cloud environments. Here are some of the key benefits of implementing a CWPP:
1. Visibility and Control: One of the primary benefits of a CWPP is the ability to gain visibility into all workloads running in the cloud and maintain control over them. With a centralized platform for workload security, organizations can monitor and manage their cloud workloads effectively, ensuring that all security policies and configurations are in place to protect against potential threats.
2. Threat Detection and Response: CWPP solutions are equipped with advanced threat detection capabilities that enable organizations to identify and respond to security incidents in real-time. By leveraging machine learning and behavioral analytics, CWPPs can detect abnormal activities and potential threats, allowing security teams to take immediate action to mitigate risks and prevent data breaches.
3. Compliance Monitoring and Reporting: In addition to threat detection, CWPPs also provide robust compliance monitoring and reporting features that help organizations stay in line with industry regulations and standards. These platforms can automatically assess workload configurations against security best practices and compliance requirements, generating detailed reports and alerts for any non-compliant activities. This ensures that organizations can maintain a strong security posture and demonstrate compliance to auditors and regulators.
By implementing a CWPP, organizations can enhance their overall security posture in the cloud, reduce the risk of data breaches, and improve their regulatory compliance efforts. With the visibility, control, threat detection, and compliance monitoring capabilities of a CWPP, organizations can confidently leverage cloud technologies while keeping their workloads and data secure.
Best Practices for Securing Workloads with CWPP
When it comes to securing workloads with Cloud Workload Protection Platforms (CWPP), there are several best practices that organizations should follow. CWPPs are essential tools for protecting cloud workloads against various threats, including malware, ransomware, and unauthorized access. By implementing these best practices, organizations can enhance the security of their workloads and minimize the risk of a data breach.
1. Comprehensive Security Assessment: Before deploying a CWPP, it is crucial to conduct a comprehensive security assessment of your cloud workloads. This assessment will help identify any vulnerabilities or weaknesses in your infrastructure that could be exploited by attackers. By understanding the security posture of your workloads, you can prioritize security measures and effectively protect your data.
2. Regular Patch Management: Keeping your cloud workloads up-to-date with the latest patches is essential for maintaining security. Most cyber attacks exploit known vulnerabilities that could be easily mitigated with timely patching. Automating patch management processes can help ensure that your workloads are always protected against known threats.
3. Network Segmentation: Implementing network segmentation is a critical practice for enhancing the security of your cloud workloads. By dividing your network into separate segments, you can isolate sensitive data and applications from potential threats. This helps contain security incidents and prevents attackers from moving laterally within your infrastructure.
4. Continuous Monitoring and Incident Response: One of the most important best practices for securing workloads with CWPP is to implement continuous monitoring and incident response capabilities. Monitoring your workloads in real-time allows you to detect suspicious activities and respond to security incidents promptly. By leveraging advanced threat detection technologies, such as machine learning and behavioral analysis, you can effectively identify and mitigate threats before they impact your operations.
5. Encryption and Data Protection: Encrypting data at rest and in transit is essential for protecting sensitive information stored in your cloud workloads. By implementing strong encryption algorithms and key management practices, you can prevent unauthorized access to your data and ensure its confidentiality. Additionally, implementing data loss prevention (DLP) measures can help prevent data leaks and maintain compliance with data protection regulations.
6. Secure Configuration Management: Properly configuring your cloud workloads is crucial for minimizing security risks. Implementing secure configuration management practices, such as disabling unnecessary services and applying least privilege access controls, can help reduce the attack surface and prevent potential security breaches. Regularly auditing your configurations and remediating any misconfigurations are essential for maintaining a strong security posture.
By following these best practices for securing workloads with CWPP, organizations can effectively protect their cloud environments against a wide range of cyber threats. Implementing a proactive security strategy that combines advanced technologies, regular assessments, and continuous monitoring is key to mitigating risks and ensuring the confidentiality, integrity, and availability of your data.
Top CWPP Solutions in the Market
When it comes to Cloud Workload Protection Platforms (CWPP), there are several solutions available in the market that offer top-notch protection for cloud workloads. These solutions help organizations secure their cloud environments by providing advanced threat detection, real-time monitoring, and automated response to potential security risks. Here are some of the top CWPP solutions that are currently leading the market:
1. VMware AppDefense: VMware AppDefense is a robust CWPP solution that offers advanced security features to protect cloud workloads. It uses machine learning and behavioral analytics to detect and respond to threats in real-time, ensuring that your cloud environment remains secure at all times.
2. Microsoft Azure Security Center: Microsoft Azure Security Center is another top CWPP solution that provides comprehensive security for cloud workloads on the Azure platform. It offers centralized security management, threat intelligence, and advanced analytics to help organizations detect and respond to security threats effectively.
3. McAfee MVISION Cloud: McAfee MVISION Cloud is a leading CWPP solution that offers cloud security for SaaS, PaaS, and IaaS environments. It provides real-time protection, data loss prevention, and threat detection capabilities to help organizations secure their cloud workloads and data effectively.
4. Check Point CloudGuard: Check Point CloudGuard is a powerful CWPP solution that offers multi-layered security for cloud workloads. It provides advanced threat prevention, network security, and compliance management features to help organizations protect their cloud environments from cyber threats.
5. Fortinet FortiGate Cloud: Fortinet FortiGate Cloud is a top CWPP solution that delivers advanced security capabilities for cloud workloads. It offers integrated threat intelligence, automated response, and sandboxing features to help organizations secure their cloud environments from evolving cyber threats. With Fortinet FortiGate Cloud, organizations can gain visibility into their cloud workloads, detect potential security risks, and respond to incidents promptly to prevent data breaches and unauthorized access.
These are just a few of the top CWPP solutions in the market that organizations can consider to enhance the security of their cloud workloads. Each of these solutions offers unique features and capabilities to help organizations protect their cloud environments effectively. By investing in a reliable CWPP solution, organizations can ensure that their cloud workloads remain secure and compliant with industry regulations.